Security researchers warn that a sprawling fraud operation known as OPCOPRO is trapping mobile users inside wholly fabricated digital ecosystems, using artificial intelligence to construct convincing but fake investment communities that groom victims over weeks before stealing their identities and money. According to the report by Check Point, the “Truman Show” scam marks a shift from malware-based attacks to social-engineering campaigns that manufacture trust through synthetic interaction. [1][3]
The scheme typically begins with an innocuous SMS impersonating a reputable financial institution. Check Point’s analysis and reporting by CyberNews show messages purporting to come from firms such as Goldman Sachs, promising extraordinary returns and directing recipients to a link that enrolls them into a private WhatsApp group. Goldman Sachs has denied that such messages are legitimate, researchers said. [1][3][2]
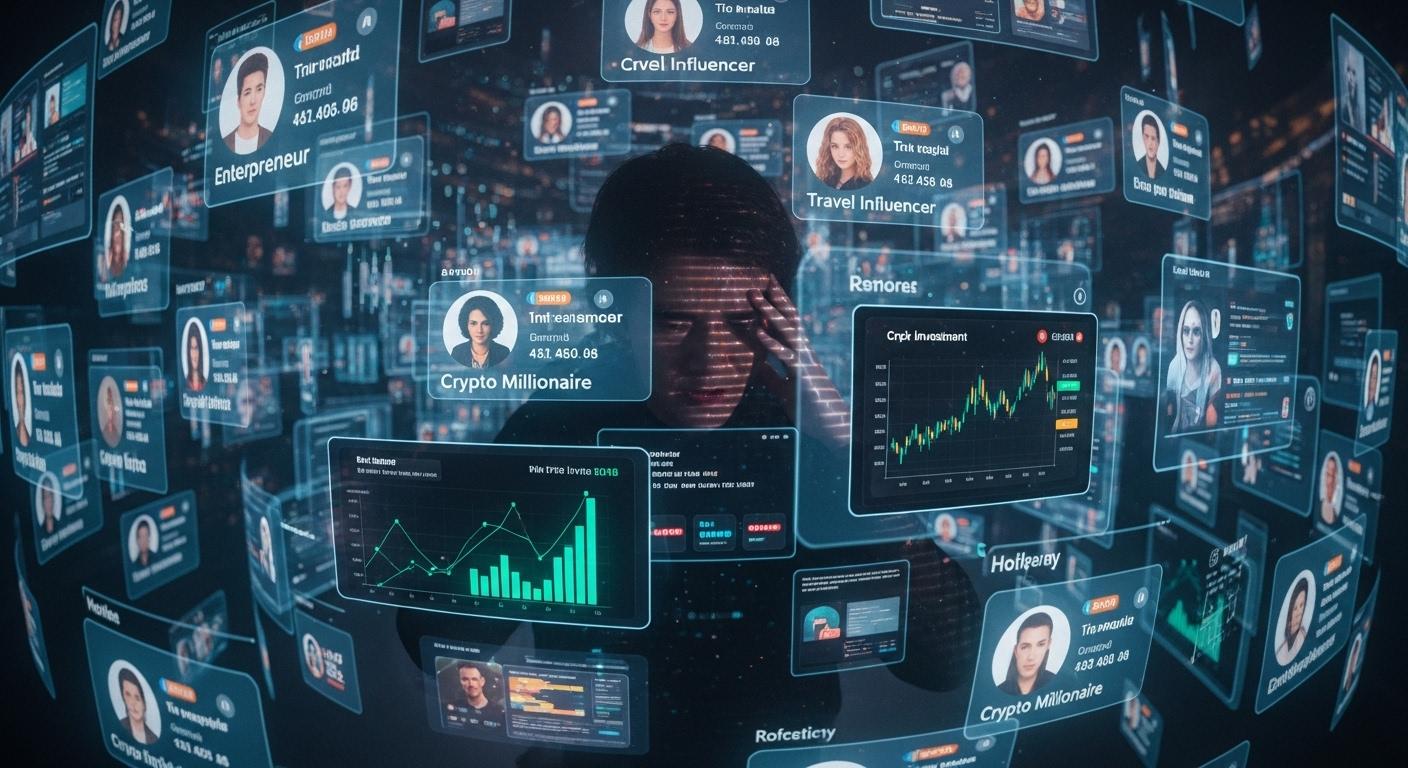
Inside the group, AI-generated personas lead the performance. Victims encounter characters such as “Professor James” and “Lily,” whose profile images and dialogue are synthetic. The chatroom is populated largely by automated accounts that echo the same praise, post fabricated profit screenshots and simulate a bustling community to normalise the scheme and pressure newcomers to invest. Many of the member numbers are internet-based and unreachable by phone, a further sign of inauthenticity, Check Point found. [1][2][3][4]
After several weeks of rapport-building, victims are steered towards downloading a bespoke app, distributed via the Apple App Store and Google Play Store in a version identified on Android as com.yme.opcopro, and asked to complete a KYC process that includes uploading identity documents and a liveness selfie. According to Check Point and corroborating coverage, the operators even present counterfeit cooperation agreements and claim partnerships with established financial firms to deepen credibility. Once supplied, identity documents and facial images become powerful tools for fraud. [1][3][2]
The mobile applications themselves provide no real trading infrastructure. Check Point’s technical analysis shows they are essentially WebView shells that display whatever fabricated balances and returns the operators choose, while all actual deposits are siphoned away. With victims’ identity documents and selfies, criminals can execute downstream attacks such as SIM swaps, social-engineering corporate helpdesks and account takeovers, turning a single interaction into broad personal and organisational compromise. [1][3]
Industry observers say the model is “industrialised”: everything from AI-generated personas to multi-language deployment and app-store distribution can be scaled and reused, lowering the cost of launching new campaigns and enabling rapid geographic spread. Infosecurity Magazine and CyberNews underline that the approach can be adapted to different languages and jurisdictions, making detection and takedown more challenging. [4][2][3]
Platforms have responded with large-scale removals and new safety measures. Meta and WhatsApp announced aggressive action earlier in 2025, removing millions of scam-linked accounts and introducing prompts to warn users when they are added to group chats by unknown contacts. Meta said more than 6.8 million scam accounts linked to fraudulent activity were taken down in the first half of 2025, a move aimed at disrupting precisely this kind of synthetic-community fraud. [5][6][7]
The rise of the “Truman Show” scam underscores the intersection of AI and social engineering as the next frontier of cybercrime, analysts say. According to the report by Check Point, defenders will need a combination of platform-level detection, stricter app-store vetting, and public awareness, particularly about sharing identity documents and responding to unsolicited links, to blunt the impact of these synthetic realities. [3][1][4]
##Reference Map:
- [1] (HackRead) - Paragraph 1, Paragraph 2, Paragraph 3, Paragraph 4, Paragraph 5, Paragraph 8
- [2] (CyberNews) - Paragraph 2, Paragraph 3, Paragraph 4, Paragraph 6
- [3] (Check Point blog) - Paragraph 1, Paragraph 2, Paragraph 3, Paragraph 4, Paragraph 5, Paragraph 8
- [4] (Infosecurity Magazine) - Paragraph 3, Paragraph 6, Paragraph 8
- [5] (The Washington Post) - Paragraph 7
- [6] (CoinLive) - Paragraph 7
- [7] (The Washington Post) - Paragraph 7
Source: Noah Wire Services